Hidding IP Address
IP stands for Internet Protocol and IP address is the address that is assigned to each device connected in computer network that use internet protocol (TCP/IP).
This IP address is used to determine the device location in the network.
The designers designed Internet Protocol Version 4 (IPv4) and IPv6 as addressing methods. IP addresses are binary numbers, but they are usually stored in text files and displayed in human readable notations, such as 172.16.254.1 (for IPv4), and 2001:db8:0:1234:0:567:8:1 (for IPv6).
IPv4 was designed as a 32bit number system. For example in 172.16.254.1, 172 stands for 10101100 binary number which is of 8 bits and it contains four such 8-bit numbers which total constitute of 32-bit. IPv4 is most widely used system for addressing. Here every number separated by dot can be of range between 0 to 255. For example 216.3.128.1 can IPv4 address.
Due to numerous growth of internet and because of the predicted depletion of available address IPv6 was designed in 1955.
How does IP address will come in use for you ?
You can use IP address of website in your browser address bar instead of domain name. It has its many uses in hacking, as with IP address you can watch out for open and closed ports for particular system which can be very important from hacker point of view. Although we can say that you can not hack any network without its knowledge.
How ever you should remember that your internet device also has an IP address which is recorded by many websites you go through. Also it can be used for your identification. So always remember to hide your IP address to another location before any type of network hacking.
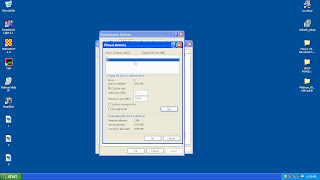
As you can see below is your traced IP address information by this blog.
So always hide your IP before any network database hacking such as DNS poisoning, SQL injection, Cross-site scripting etc.
How to hide IP address ?
There are ways to hide your IP address manually using command prompt combining your routers configuration. But this will not be safe also it will be very complicated to implement, but let the software should do this for you. It is very easy to hide your IP address by using software, there are many software present for you to use. Search on google for it, also some of its example is Platinum Hide, Hide my IP, Easy-Hide-IP etc. Also don't worry using these software is very safe.
This IP address is used to determine the device location in the network.
The designers designed Internet Protocol Version 4 (IPv4) and IPv6 as addressing methods. IP addresses are binary numbers, but they are usually stored in text files and displayed in human readable notations, such as 172.16.254.1 (for IPv4), and 2001:db8:0:1234:0:567:8:1 (for IPv6).
IPv4 was designed as a 32bit number system. For example in 172.16.254.1, 172 stands for 10101100 binary number which is of 8 bits and it contains four such 8-bit numbers which total constitute of 32-bit. IPv4 is most widely used system for addressing. Here every number separated by dot can be of range between 0 to 255. For example 216.3.128.1 can IPv4 address.
Due to numerous growth of internet and because of the predicted depletion of available address IPv6 was designed in 1955.
How does IP address will come in use for you ?
You can use IP address of website in your browser address bar instead of domain name. It has its many uses in hacking, as with IP address you can watch out for open and closed ports for particular system which can be very important from hacker point of view. Although we can say that you can not hack any network without its knowledge.
How ever you should remember that your internet device also has an IP address which is recorded by many websites you go through. Also it can be used for your identification. So always remember to hide your IP address to another location before any type of network hacking.
As you can see below is your traced IP address information by this blog.
So always hide your IP before any network database hacking such as DNS poisoning, SQL injection, Cross-site scripting etc.
How to hide IP address ?
There are ways to hide your IP address manually using command prompt combining your routers configuration. But this will not be safe also it will be very complicated to implement, but let the software should do this for you. It is very easy to hide your IP address by using software, there are many software present for you to use. Search on google for it, also some of its example is Platinum Hide, Hide my IP, Easy-Hide-IP etc. Also don't worry using these software is very safe.